The recent compromise of the email accounts of U.S. Government officials has been widely reported. As the New York Times reported, these emails appeared to come from trusted colleagues. The content was consistent with what was expected from real emails. Because of the apparent source of the emails and the relevant content, the recipient was deceived into taking compromising actions.
How hard is it to create a compelling email? What do these spear-phishing emails look like? We find the answer at contagio, where several examples of these malicious emails are posted. Here are two:


The first example shows how the content was carefully conceived and drafted to appear authentic. The attachment also appears authentic and is consistent with the text.
The second example shows just how easy it is to deceive someone. By merely faking a trusted from email address and using a vague, but relevant, subject, the attachment was imbued with enough credibility to deceive the recipient into opening it.
In response to schemes such as this, Iconix has released SP Guard.
SP Guard modifies the email client’s display to provide a visual indicator of the identity of the sender of email. This is an example from Outlook, the popular business email client, in which a company called “MyCo” is marking their internal messages as well as those from trusted partners such as their law firm. Note especially the last message, though seemingly benign, is a spear-phishing message and is not marked as authentic:
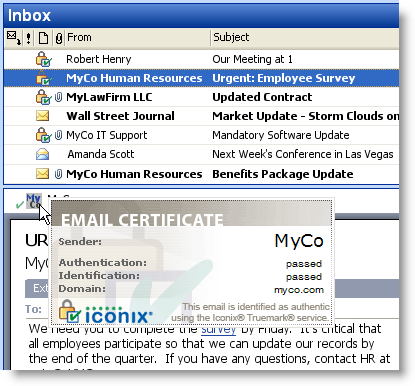
SP Guard provides the email recipient with three easy to recognize confirmations that a message is really an internal email or from a trusted counterpart:
- List View. There is an integrity indicator in the list view of the email client.
- Message. The open message has a further indicator of authenticity.
- Mouseover. Mousing over the authentication indicator in the message prompts the display of a certificate that further identifies the sender.
SP Guard is available now from Iconix.
To learn more, visit us at http://www.iconix.com/business/spearphishing.php.



 Posted by iconixtruemark
Posted by iconixtruemark 