Antivirus software does not work against Advanced Persistent Threats. In the realm of Advanced Persistent Threats, the malware is targeted and designed for each intended victim.

The attackers are hard at work creating new malware. According to Bit9:
Furthermore, AV signature-based libraries are growing at 50,000 a day, with current libraries anywhere from 6 to 20 million signatures. At this pace, basing endpoint security solely on AV libraries is unsustainable in terms of sheer volume and efficient endpoint scanning – as well as a drain on IT resources. Some AV vendors now recommend downloading selective signature packs, belying the scalability problem. But more important is currency:
No endpoint security paradigm looking for known malware can detect the not-yet-known, dynamically changing, advanced threat.
In its Second Annual Cost of Cybercrime Study, Ponemon Institute summarized the time it takes to resolve different categories of cyberattack:

Ponemon Institute noted in footnote 12 of the report that the classifications are not independent. It has been clearly established that one of the most effective ways to introduce malicious code into an organization is phishing.
Ponemon Institute estimated the cost of an unresolved cyberattack at $22,986 per day. At Iconix we agree with Bit9 and Ponemon on the importance of technologies that permit rapid detection of attacks so that the damage can be limited. However, as the old saying goes, an ounce of prevention is worth a pound of cure. How do you prevent hackers from deceiving employees with highly targeted socially engineered emails?
In order to prevent social engineering from deceiving the email recipient, SP Guard from Iconix modifies the email client’s display to provide a visual indicator of the identity of the sender of email. This is an example from Outlook, the popular business email client, in which a company called “MyCo” is marking their internal messages as well as those from trusted partners such as their law firm. Note especially the last message, though seemingly benign, is a spear-phishing message and is not marked as authentic:
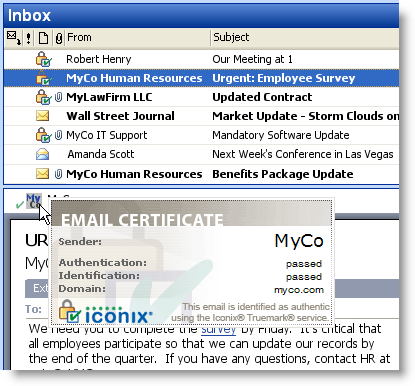
SP Guard provides the email recipient with three easy to recognize confirmations that a message is really an internal email or from a trusted counterpart:
- List View. There is an integrity indicator in the list view of the email client.
- Message. The open message has a further indicator of authenticity.
- Mouseover. Mousing over the authentication indicator in the message prompts the display of a certificate that further identifies the sender.
SP Guard is available now from Iconix. For further information, contact us at 408-727-6342, ext 3 or use our online form.



 Posted by iconixtruemark
Posted by iconixtruemark 