IBM has just released its IBM X-Force® 2011 – Mid-year Trend and Risk Report. The IBM Press Release provides a good summary of the 92 page report.
For those of us who are interested in phishing and spearphishing, IBM’s report provides some interesting insights.
The report draws a clear distinction between phishing and spearphishing. The report reminds us that while the terms are similar, the schemes are vastly different. In phishing, the bad guy is playing a game of numbers:
Phishing derives its name from the analogy of fishing in a large lake. You cast your line into that lake and you do not care if there are 10,000 fish in there that do not find your bait tasty. You also do not care if you catch the biggest fish in the lake. All you care about is the half a dozen or so reasonably sized fish who will take the hook and make your dinner. Your dinner is in numbers, not size. …
Phishing relies on mass mailings with relatively little personalization beyond, possibly, a customized address in the “to” field and maybe a name in the subject and message body. They are often sent in bulk from botnets and mass mailers. Phishing may look rather unprofessional with a number of spelling or grammatical errors. It may appear to come from an institution with which the recipient may or may not have a business relationship. Many of these types of things may serve as red letter warnings that this email is not legitimate. Often, phishing attacks lead the users to malware, like fake Anti-Virus and Trojans, or malicious URLs run by attackers trying to hijack connections. Because they are mass mailings, the various security organizations and services rapidly pick up on the malicious sites, URLs, and software and it is quickly detected. The people behind phishing really do not spend a lot of time preparing these messages and their sites may only be up for a few hours before they are taken down by security organizations. Senders of phishing emails really do not care if 99.99 percent of the people receiving the email trash them.
In spearphishing, the bad guy is playing a patient game of precision targeting:
Spear phishing is highly directed and targeted at relatively few and very specific individuals within an organization. Spear phishing is deeply customized and personalized to make it appear as though it has come from a legitimate friend or business colleague. The attackers know the targets well and may spend considerable time and effort in studying these targets and crafting the attacks. It probably will not appear to be a generic message from a large institution. Rather, it may seemingly come from an individual friend or colleague with whom there has been frequent past messages. It may even relate to recent events or activities both individuals would know about. The message itself may not even be “spoofed” but may actually come from the other individual’s compromised account. The malware or malicious site the email leads to will not have been mass mailed so the security and anti-virus organizations may be unaware of the sites and software. In short, these people have picked their targets and tools carefully. The attackers have decided they want you and have put a great deal of effort into getting you. Consequently, it must be worth the while of the attackers. The yield percentage must be much higher, 0.01 percent success is just not going to cut it. The attackers require a significant percentage of the targets to fall for the trap. The value of the target also must be much higher, to provide a better “return on investment”.
To extend the fishing analogy, this is the fisherman standing, spear in hand, in the water, on a dock, or in a boat, watching a really big fish he wants. He waits patiently while watching the fish’s movements and learning those movements. When the time is right, the spear phisher acts quickly and decisively either getting the fish or not. If not, he picks another fish or another spear. A lot of time and effort goes into this type of fishing. His dinner is more about the size of the fish rather than the number of fish.
Later in the report, IBM discusses one of our favorite subjects — the fallacy that in phishing and spearphishing the real problem is stupid users.
When the subject of phishing and spear phishing comes up, invariably someone will ask “how could anyone be so stupid?” That question may be understandable for common phishing. It is not quite so applicable to spear phishing and APTs, however. Spear phishing and APTs are highly sophisticated. They are not so easy to identify.
We have many common derogatory terms used in cases where someone makes a mistake and falls for a trap such as “operator headspace,” “the nut that holds the keyboard,” “PEBKAC” (Problem Exists Between Keyboard And Chair, or “PICNIC” (Problem In Chair, Not In Computer). These terms are summed up in a comment we see in a lot of presentation slides when it comes to human error—“There is no patch for stupid.” But, these terms may disregard the sophistication of a number of these attacks and doing an injustice to some of the individuals ensnared. They may even be making the problem worse.
By categorizing these problems as such we may be giving people a false sense of confidence that they would never fall for something like that. They won’t be stupid. But the attackers are not stupid either and they are picking their targets carefully and crafting their attacks. The person who falls for these may not have been stupid but merely unprepared and they may have been unprepared because of excessive references to these being stupid.
By categorizing these problems as such, we may put victims on the defensive. They have heard the snide remarks and here they are or they suspect (but are not sure) that something bad might have happened to them. Do they dare tell anyone and risk ridicule for falling for a trap? They should be encouraged to report anything out of the ordinary. We should be cautious about terminology and emphasize that some of these attackers are good and getting better.
The social engineering discussion ends with the admonition that defense includes training, monitoring and remediation. While we certainly agree with that, the evidence is clear that training is inadequate to deal with sophisticated social engineering schemes.
Social engineering deceives the users into becoming the agents of the criminals. What can be done to defend the enterprise against spear-phishing? The enterprise can adopt a tool that identifies trusted email so that the target of the spear-phishing attack can distinguish real email from fake email. That tool is SP Guard from Iconix.
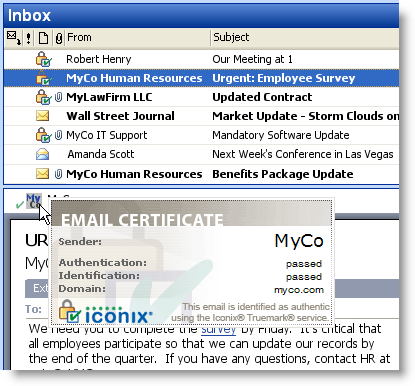
SP Guard provides the recipient with three confirmations that a message is real:
- List View. There is an integrity indicator in the list view of the email client.
- Message. The open message has a further indicator of authenticity.
- Mouseover. Mousing over the authentication indicator in the message prompts the display of a certificate that further identifies the sender.
SP Guard now offers a fraud filtering enhancement. This additional protection is becoming increasingly important given the latest generation of highly targeted spear-phishing emails which are so well crafted that users cannot tell real from fake.
SP Guard is available now from Iconix. For further information, contact us at 408-727-6342, ext 3 or use our online form.



 Posted by iconixtruemark
Posted by iconixtruemark 