backtosecurity.com has written a step by step description of how it used social networking data that it discovered on Facebook to craft a spearphishing attack on an Australian advertising agency. This was a whitehat hack.
The posting describes how the hacker used information from the target’s website to learn about the management structure and key names. The hacker then correlated the employee names with Facebook profiles to locate a likely person to exploit. The hacker targeted an executive’s assistant for the attack. The hacker was able to easily determine which executives of the firm did not have Facebook accounts. The hacker set up a Facebook account masquerading as an executive who was new to Facebook and used this new Facebook account to “friend” the targeted employee. Yes, people use Facebook at work. Exploiting the trust that was gained as a Facebook friend, the hacker was then able to take control of the target computer. On the assumption that this assistant logged into her supervisor’s email account, the hacker searched the assistant’s machine for supervisor’s credentials. And found the supervisor’s passwords.
In a second posting, backtosecurity.com explains how social networking can be used to discover email addresses. In this posting, backtosecurity.com summarizes the spearphishing problem:
Spear Phishing attacks can have numerous ‘end games’ associated with them. This has been the most popular method in recent times for hackers to gain access to huge corporations and banks. Usually with the goal of stealing private company information to stealing millions of customer’s credit card numbers which are then sold on the cyber black-market.
What makes Spear Phishing so successful is the fact that you are exploiting human weaknesses more so than technical weaknesses. If a company spends hundred of thousands of dollars on the latest state of the art Firewalls, Intrusion Detection/Prevention technologies and expensive all in one Anti Virus suites their users, then they may operate on a misguided sense of security.
What happens if a staff member receives an email or a social network request from somebody they believe they know and which seems legitimate? If they click on this link or open this attachment, then those hundreds of thousands of dollars of security equipment is now pointless.
backtosecurity.com provides a powerful reminder that social engineering deceives the email recipients into becoming the agents of the criminals. What can be done to defend the enterprise against spearphishing? The enterprise can adopt a tool that identifies trusted email so that the target of the spearphishing attack can distinguish real email from fake email. That tool is SP Guard from Iconix.
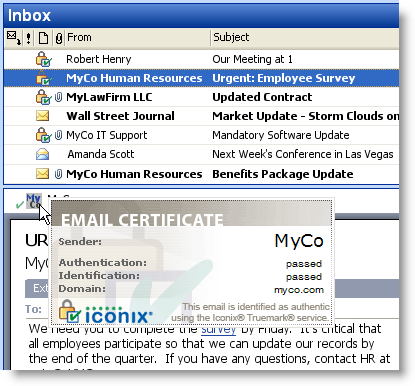
SP Guard provides the recipient with three confirmations that a message is real:
- List View. There is an integrity indicator in the list view of the email client.
- Message. The open message has a further indicator of authenticity.
- Mouseover. Mousing over the authentication indicator in the message prompts the display of a certificate that further identifies the sender.
SP Guard now offers a fraud filtering enhancement. This additional protection is becoming increasingly important given the latest generation of highly targeted spear-phishing emails which are so well crafted that users cannot tell real from fake.
SP Guard is available now from Iconix. For further information, contact us at 408-727-6342, ext 3 or use our online form.
![]()
![]()



 Posted by iconixtruemark
Posted by iconixtruemark 