Last weekend the world’s largest hacking convention, Defcon, was held in Las Vegas. Reuters reported on the conference:
[H]ackers taking part in the competition on Friday and Saturday found it ridiculously easy in some cases to trick employees at some of the largest U.S. companies to reveal information that can be used in planning cyber attacks against them.
This was the second year that Defcon included a contest in “social engineering,” in which the hackers tried to deceive people into disclosing information or taking ill-advised actions, such as opening an infected attachment, downloading malware or visiting a malicious website. The most frequently used social engineering hack is spearphishing, in which the hacker impersonates a friend, colleague or other convincing sender (one such hack involved the impersonation of President Obama). In the successful spearphishing attack, the impersonation and its call to action deceive the recipient into disclosing information or compromising the recipient’s system. Recent examples of successful spearphishing attacks include Epsilon (the email marketing company), U.S. defense contractors, the French Finance Ministry, the IMF, EMC’s RSA Security division and government agencies around the world.
The Reuters article states that the success of social engineering hacks is because employees are poorly trained. While there are no doubt cases where social engineering schemes could be overcome with training, the successful spearphishing campaign is driven by the guile of the perpetrator, not the training deficiencies of the victim.
Training people to avoid suspicious emails is essentially impossible because, as Lt. Col. Gregory Conti, IT professor at West Point observed in the New York Times,
“What’s ‘wrong’ with these e-mails is very, very subtle,” he said, adding: “They’ll come in error-free, often using the appropriate jargon or acronyms for a given office or organization.”
The tools to improve the criminals’ craft are becoming more robust every day. A little internet research yields substantial personal information that can be used to deceive the recipient. Email is the ideal medium for deception because the attacker has at his command all of the human factors needed to deceive the recipient. Given the ability of criminals to craft and deliver deceiving emails, email recipients are essentially unarmed in this battle of wits with spearphishers.
Social engineering deceives the users into becoming the agents of the criminals. What can be done to defend the enterprise against spear-phishing? The enterprise can adopt a tool that identifies trusted email so that the target of the spear-phishing attack can distinguish real email from fake email. That tool is SP Guard from Iconix.
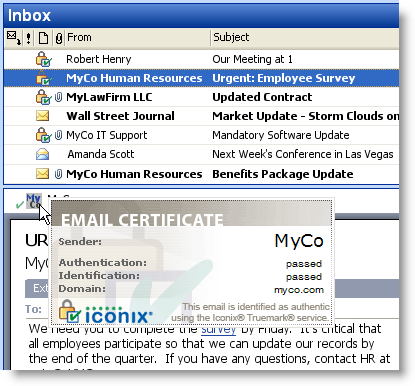
SP Guard provides the recipient with three confirmations that a message is real:
- List View. There is an integrity indicator in the list view of the email client.
- Message. The open message has a further indicator of authenticity.
- Mouseover. Mousing over the authentication indicator in the message prompts the display of a certificate that further identifies the sender.
SP Guard is available now from Iconix. For further information, contact us at 408-727-6342, ext 3 or use our online form.



 Posted by iconixtruemark
Posted by iconixtruemark 